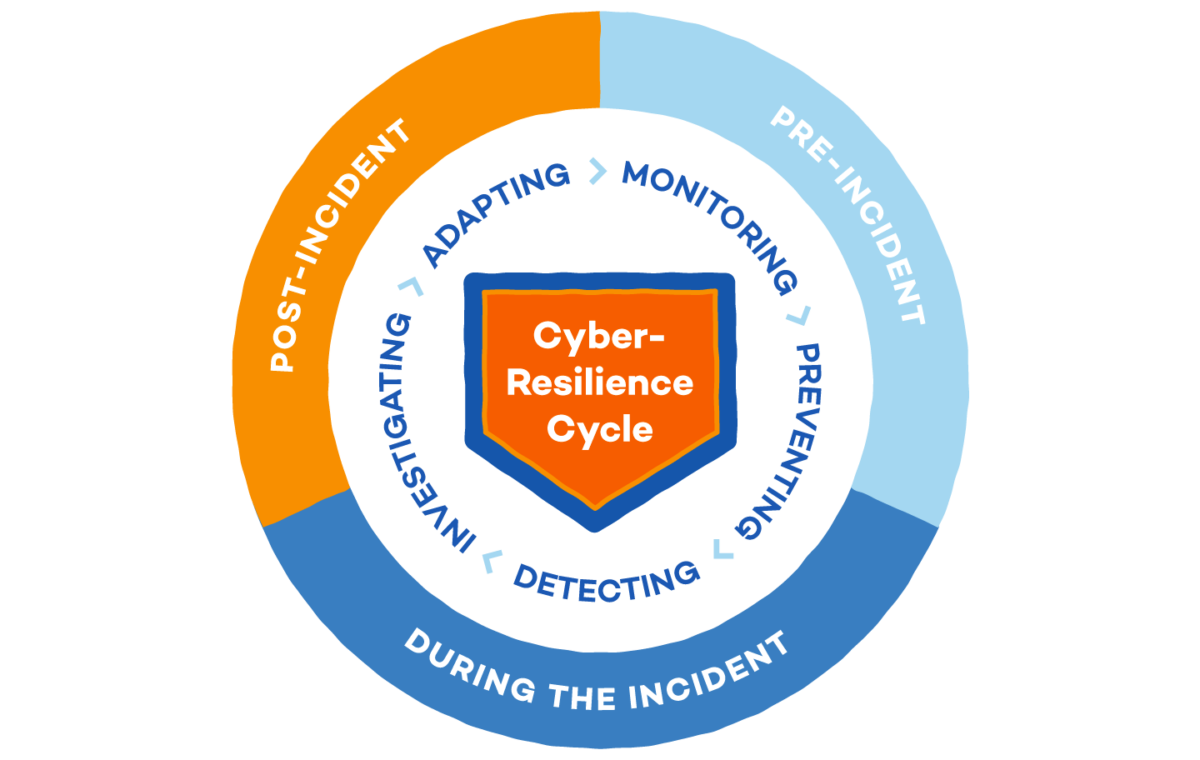
You don’t need ransomware to suffer a breach. Sometimes, the biggest threat is the quiet one—the open port, the misconfigured remote access, the shadow IT that no one owns. Remote Desktop Protocol (RDP)—a core tool for remote work—has become a top attack vector for threat actors, especially when exposed to the internet or lacking MFA. For SMBs balancing budget constraints with remote access needs, the risk is real—and rising.