Gootloader: The Malware Targeting SMBs Through SEO Poisoning
It doesn’t take a massive ransomware gang to cripple your business. Sometimes, all it takes is a Google search gone wrong.
That’s the terrifying reality behind Gootloader, a stealthy malware campaign specifically engineered to lure unsuspecting SMB employees via Search Engine Optimization (SEO) poisoning. One click—and your entire network is compromised.
At ACME MSSP, we see these kinds of attacks every day. Let’s break down how it works, why it’s so dangerous to SMBs, and how XDRaaS, SOAR, and SOCaaS protect you without blowing your IT budget.
The Anatomy of the Attack:
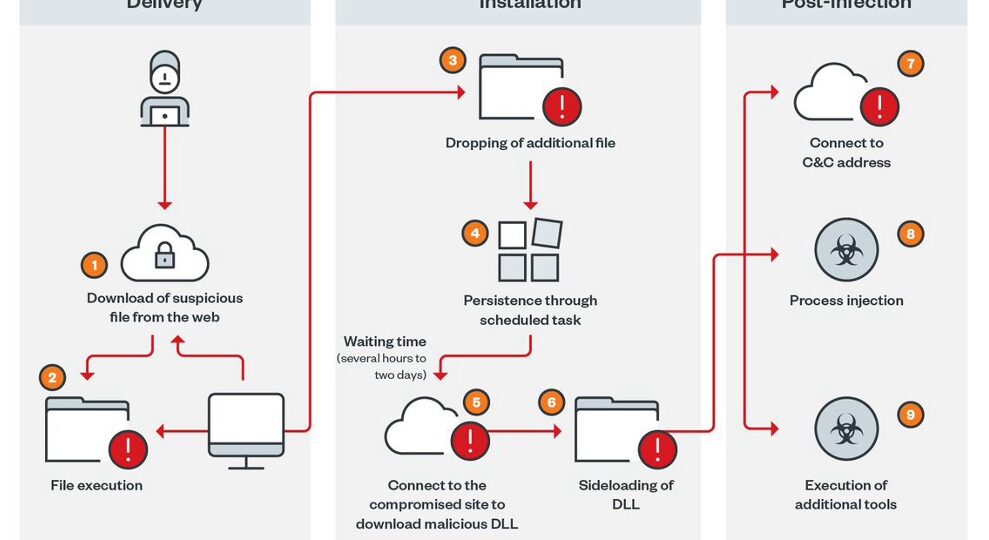
Gootloader infections typically begin when an employee searches for business-related templates or contract samples—things like “free lease agreement download” or “vendor payment terms doc.”
Here’s what happens next:
SEO Poisoning:
Malicious actors create blog posts optimized to rank on Google with those exact keywords.
Payload Delivery:
The blog links to a ZIP file containing a malicious JavaScript file masquerading as a helpful document.
Execution & Infection:
Once clicked, the JS silently downloads the Gootkit malware, often followed by Cobalt Strike, ransomware loaders, or banking trojans.
Persistence & Lateral Movement:
The malware uses registry edits and LOLBins (Living Off the Land Binaries) to persist and move laterally undetected.
Why SMBs Are the Primary Target:
SMBs often lack dedicated threat intel teams, meaning they don’t detect emerging SEO threats.
Employees have broad permissions and click on downloads out of necessity.
There’s often no sandboxing or endpoint behavior analytics.
Backups? Sometimes outdated. Detection? Often reactive. Budget? Limited.
How ACME MSSP Stops Gootloader Cold:
✅ XDRaaS
Our managed Extended Detection & Response platform detects abnormal script execution, suspicious file downloads, and C2 activity in real time.
✅ SOAR + Threat Intelligence
Gootloader indicators (IOCs, domain patterns, JS behavior) are mapped to automated playbooks that instantly isolate affected hosts, pull logs, and notify our 24/7 SOC.
✅ DNS Filtering + Web Control
We block malicious domains at the DNS level—before the browser even loads the infected page.
✅ Security Awareness Training
Employees are trained to spot shady download pages, understand SEO poisoning, and know when to report suspicious files.
Outcome:
With ACME’s managed services in place, this kind of infection never makes it past the front door. And if it does—we isolate it, auto-contain it, and roll back the damage before operations are affected.
Conclusion:
Cyber resilience for SMBs doesn’t mean outspending the bad guys—it means outsmarting them. ACME MSSP gives you that edge, blending automation, intelligence, and people into one hardened defense layer that makes attacks like Gootloader a dead end.