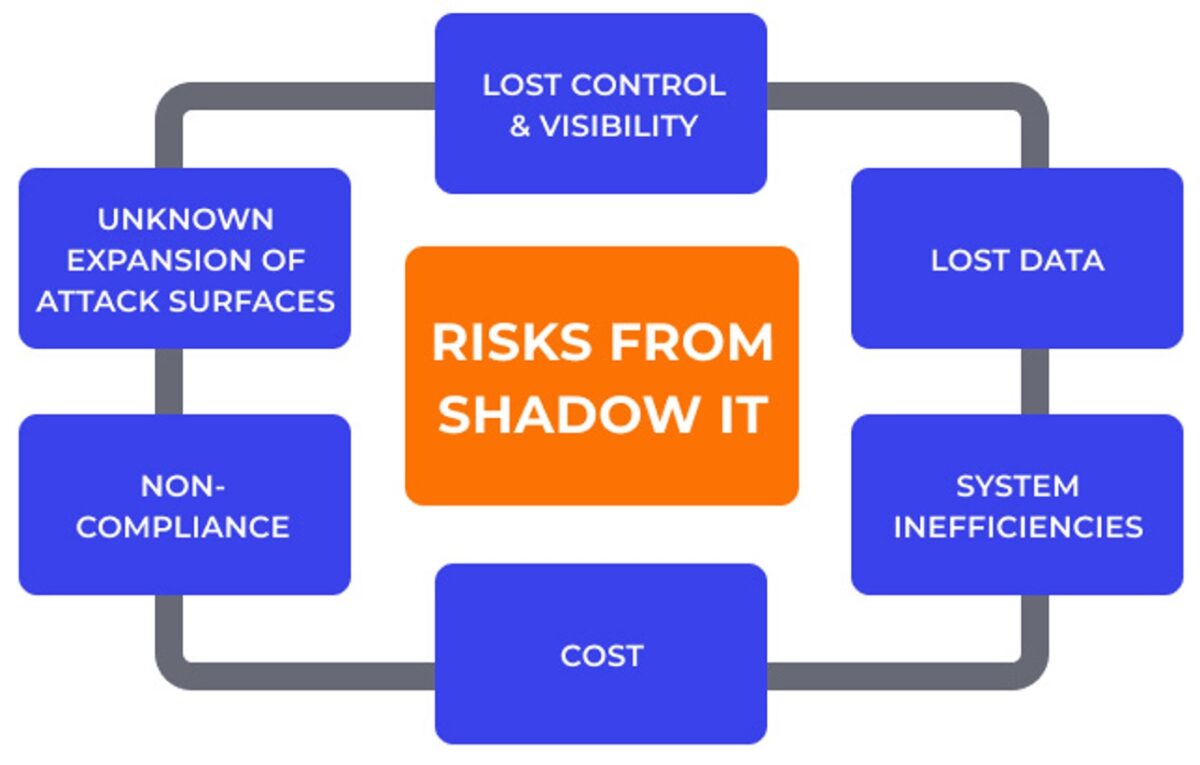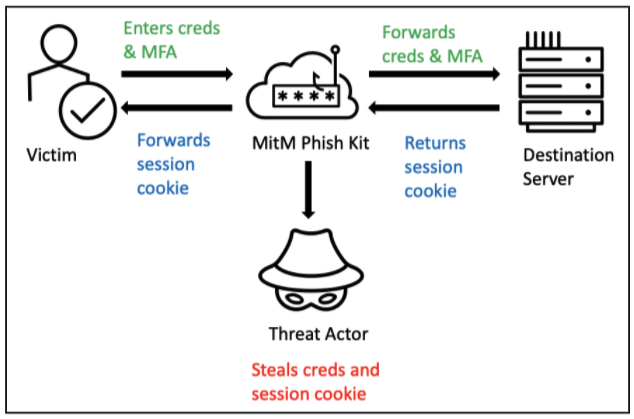
You implemented MFA and thought you were safe. Think again. Today's phishing kits are smarter, faster, and built to sidestep even modern defenses. Here's how your business can stay ahead—without stretching your security budget. For years, Multi-Factor Authentication (MFA) has been touted as the silver bullet for account security. And rightly so—MFA blocks over 99% of credential-based attacks, according to Microsoft.