Modern Threats Demand a Modern Strategy—This Framework Delivers
Cybersecurity isn’t just about tools—it’s about how you orchestrate them. Many SMBs and government agencies fall into the trap of stacking point solutions without a strategic framework. The result? Gaps in visibility, bloated budgets, and uncertainty about what’s actually working.
That’s where the Cyber Defense Matrix® comes in.
At ACME, we use this deceptively simple—but incredibly effective—model to map, measure, and mature your entire security program. Let’s break it down.
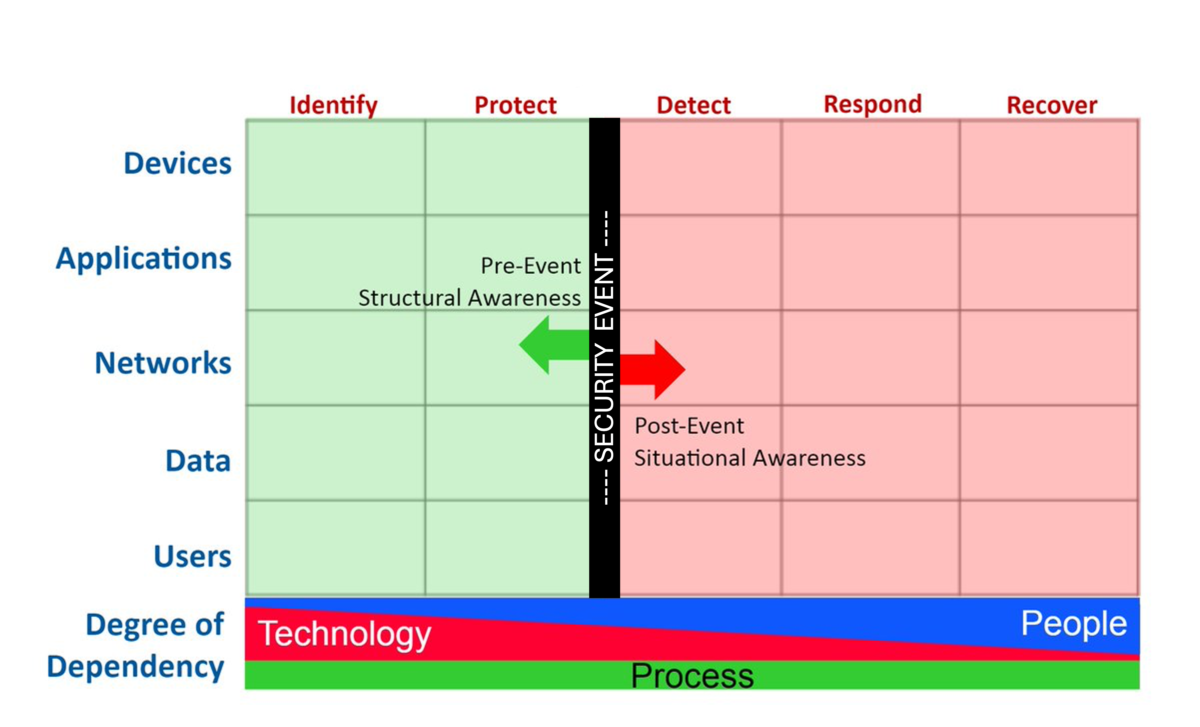
🧩 What Is the Cyber Defense Matrix®?
Created by security expert Sounil Yu, the Cyber Defense Matrix helps you organize your security tools and capabilities across five functional areas:
Identify
Protect
Detect
Respond
Recover
… and across five asset classes:
Devices
Applications
Networks
Data
Users
Imagine a grid. Now imagine placing every tool, policy, or process you use into its appropriate cell. You immediately see what’s covered—and what’s not.
📉 The Problem Most SMBs Face
SMBs and government orgs often struggle with:
Tool sprawl with overlapping features.
Over-investment in “Protect” capabilities, under-investment in “Respond” or “Recover.”
Confusion over whether compliance = security (spoiler: it doesn’t).
Limited staff trying to manage too much tech.
By aligning your operations to the Cyber Defense Matrix®, you stop guessing—and start planning.
🛠 How ACME Puts the Matrix to Work
At ACME, we use the Cyber Defense Matrix® as a blueprint to:
✅ Evaluate your existing security posture
✅ Expose blind spots and redundant tools
✅ Prioritize initiatives that reduce risk AND cost
✅ Map your tools to NIST CSF® for compliance and audit-readiness
Here’s how that looks in action:
Matrix Cell ACME MSSP Coverage
Detect – Network NDR (Network Detection & Response)
Protect – User MFA, Phishing Simulation, DNS Filtering
Respond – Devices XDRaaS + SOAR = Automated Isolation & Containment
Recover – Data Backup Strategy + Incident Playbooks
Identify – Apps Attack Surface Management (ASM)
The result? Every asset. Every function. Covered.
💡 Real-World Benefits: Why It Matters to SMBs & Government Teams
Here’s what our clients say once we implement the Cyber Defense Matrix®:
“We finally understand where our budget is going—and what it’s protecting.”
“We realized we had 3 tools doing the same thing and still had gaps.”
“Our board loved the visual clarity—we could show risk and ROI in one slide.”
This isn’t just a framework—it’s a decision-making tool that saves time, budget, and confusion.
📈 The ACME Advantage
We don’t just hand you a Matrix—we bring the solutions to fill it.
✅ XDRaaS for deep threat detection across endpoints, users, and networks.
✅ SOCaaS for 24/7 monitoring without the in-house SOC price tag.
✅ SIEM + SOAR for visibility and automated response.
✅ GRC-as-a-Service to align your security strategy with compliance and risk management.
All of it mapped back to NIST CSF and the Cyber Defense Matrix for clear, measurable progress.
🎯 Final Thoughts: Security Shouldn’t Feel Like Guesswork
If your current cybersecurity setup feels like a collection of band-aids and black boxes, you’re not alone.
The Cyber Defense Matrix® brings order to the chaos—especially when paired with a trusted MSSP like ACME. We translate frameworks into practical action, and tools into real protection.
🚀 Ready to See Where You Stand?
Let’s map your defenses and expose your blind spots—before an attacker does.
📅 Book a 30-minute consult
You’ll walk away with a Matrix-based snapshot of your security posture—zero jargon, just clarity.