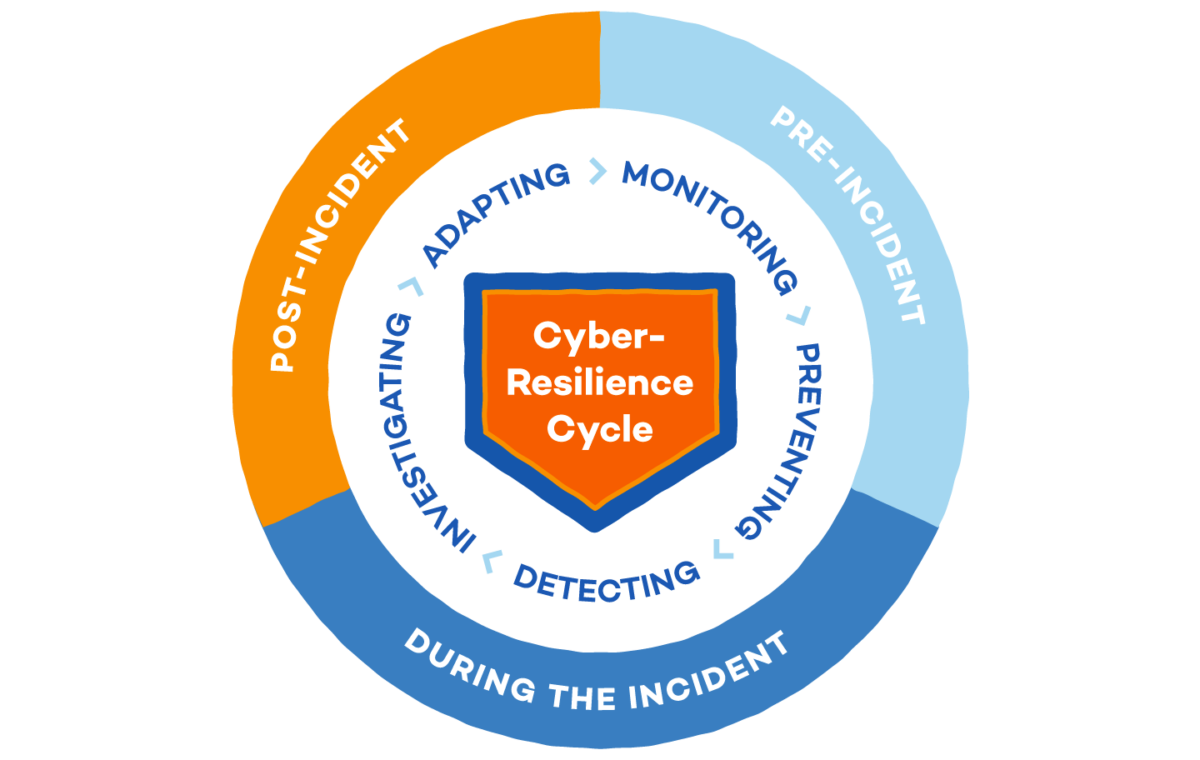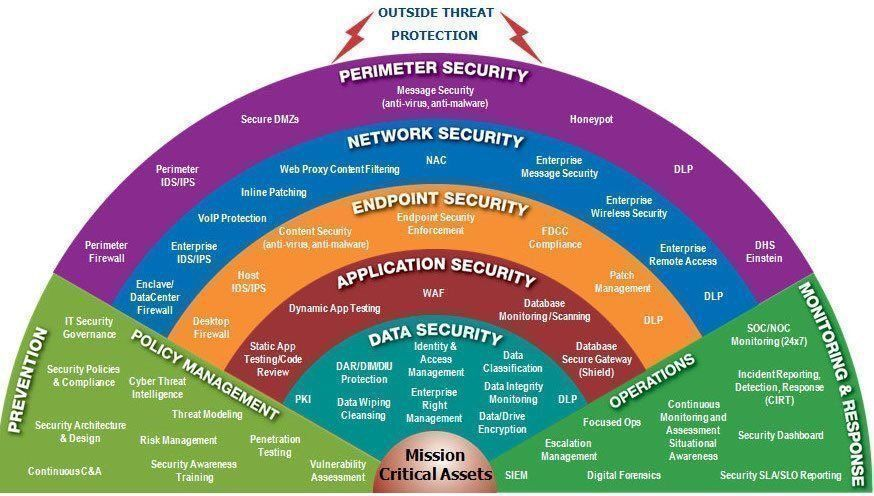
Perimeter firewalls are yesterday’s defense. Learn how modern MSSPs leverage Zero Trust, Microsegmentation, and Threat-Informed Defense to deliver resilient, scalable protection. In an era where threats don’t respect perimeters and ransomware kits are sold like SaaS, relying solely on traditional network defenses is like guarding your secrets with a picket fence.