A cyber incident doesn’t have to be the end of your reputation — it can be the start of a smarter security strategy.
Let’s be honest: cyber incidents are inevitable. But the damage doesn’t have to be. The key isn’t avoiding every breach — it’s about how you respond and what you build afterward.
Many SMBs treat incidents like isolated disasters. At ACME, we help you treat them as strategic turning points.
The Hidden Opportunity in a Breach
Every incident uncovers:
Visibility gaps
Process weaknesses
Vendor blind spots
Underperforming controls
But most organizations only plug the hole and move on. That’s a mistake.
Transforming Response into Resilience
ACME helps turn post-incident insights into long-term value through:
Automated Forensics: Our SOAR and XDR platforms document the attack chain, allowing fast triage and immediate detection improvements.
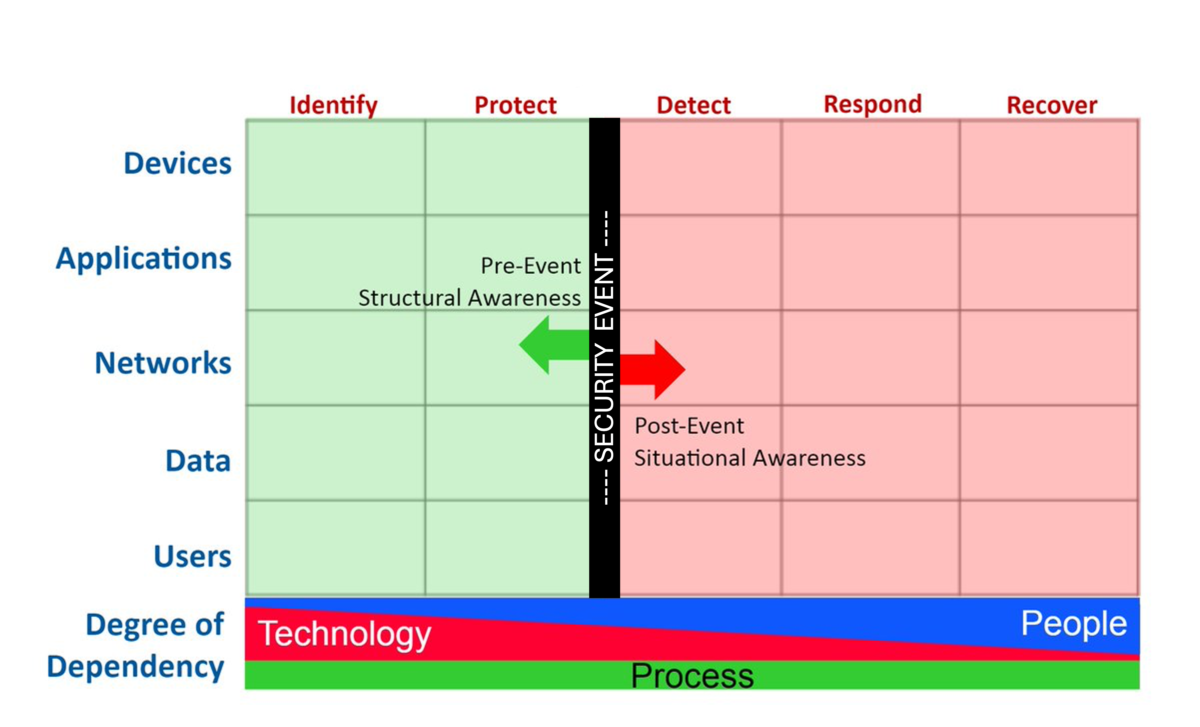
Resilience Audits: We map your tools, workflows, and risks to the NIST CSF and Cyber Defense Matrix to identify where your defenses broke down — and where they held strong.
Incident-informed GRC: We align your updated security policies with compliance frameworks, so the response improves not just security, but also regulatory posture.
Cost-Benefit ROI Models: Post-incident, we show where automation, monitoring, or segmentation would’ve reduced downtime — and what that means in dollars.
The Strategic Advantage
You don’t need to fail to learn — but if you do, fail forward.
With ACME MSSP as your partner, an incident becomes a business case for smarter controls, not a blame game. We help you show leadership, regulators, and customers that you took action — and futureproofed the business.
Make the Most of the Moment
Security isn’t just about defense — it’s about adaptability.
When the worst happens, the smartest SMBs don’t just recover — they invest, optimize, and lead. With ACME’s tailored managed services, we make sure that the cost of an incident becomes the foundation for ROI — in uptime, reputation, and cyber maturity.