Shadow IT in Small Businesses — A Silent Breach Vector That’s Growing
Introduction
As small businesses rapidly adopt cloud services and digital tools to stay competitive, they’re also unknowingly opening the door to a dangerous and growing threat: Shadow IT.
Shadow IT refers to the use of software, devices, and services without approval or oversight from your IT or security team. It’s an invisible risk — and for small and medium-sized businesses (SMBs) without full-time cybersecurity resources, it’s becoming a leading cause of data breaches, compliance violations, and operational disruption.
At Halcyon Cyberworks, we work exclusively with SMBs to illuminate these hidden risks through AI-driven, enterprise-grade protection within an affordable, user-friendly platform. In this post, we’ll show you how to identify Shadow IT in your business, understand the dangers, and take proactive steps to mitigate its impact.
What Is Shadow IT — and Why Should SMBs Care?
Shadow IT Defined
Shadow IT includes any technology, application, or device used without approval from your IT or security leadership. In SMBs, this often takes the form of:
-
Employees using personal cloud storage (like Google Drive) for client documents
-
Installing unsanctioned browser extensions or chat tools
-
Accessing work systems from personal smartphones or laptops
-
Subscribing to software services with a corporate card — without telling anyone
Why It Happens
Small businesses aren’t reckless — they’re resourceful. Shadow IT typically arises due to:
-
Speed and convenience: Employees seek tools that help them do their jobs faster
-
Lack of internal IT oversight: SMBs may lack formal policies or cybersecurity staff
-
Hybrid work environments: Personal and professional tech often blend together
-
Low awareness: Many employees don’t realize the risks or the boundaries
🔎 Nearly 50% of SMBs report that they’ve discovered cloud apps in use that their IT team didn’t know about — and 20% of breaches in small businesses are traced back to unauthorized tech usage.
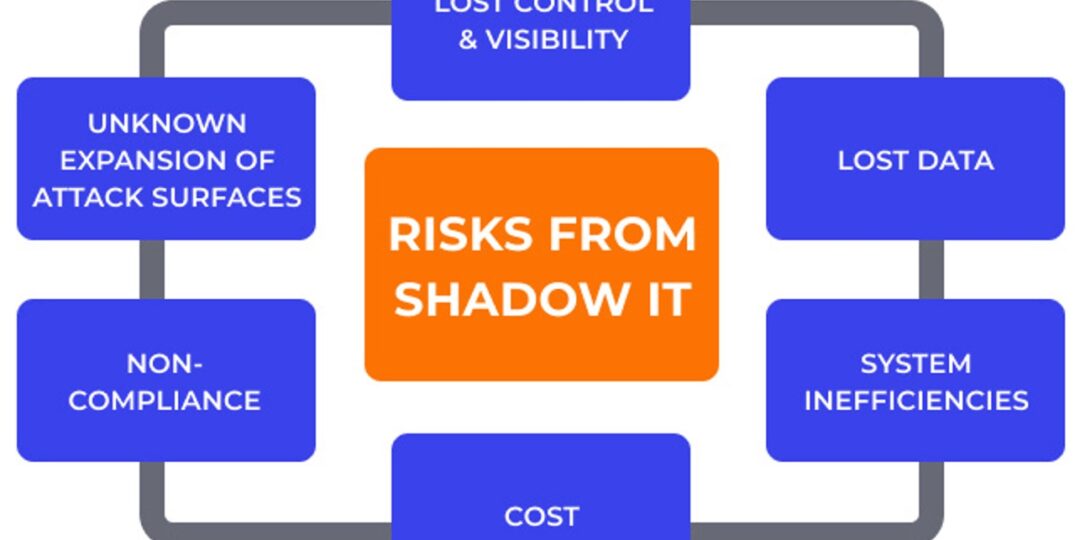
The Hidden Risks of Shadow IT
Shadow IT isn’t just an organizational nuisance — it’s a direct breach vector that bypasses your security stack. Without visibility, protection tools can’t do their job.
Key Threats to SMBs:
-
Data Breaches: Sensitive customer or financial data may be exposed or leaked
-
Regulatory Noncompliance: Violating HIPAA, PCI, or GDPR can trigger fines or legal actions
-
Increased Attack Surface: Every unauthorized app is a new door for hackers
-
Operational Disruption: Business continuity suffers when tools conflict or data is lost
Real-World Example
A small accounting firm allowed staff to use personal email to send client files during tax season. A phishing email compromised one account, exposing over 2,000 tax records — costing the firm $90,000 in cleanup, reporting, and reputation loss. All because the system lacked email protection, user behavior analytics (UEBA), and policy enforcement.
How to Recognize Shadow IT in Your Business
You can’t fix what you can’t see. Here are signs Shadow IT may already exist in your organization:
-
Employees using different versions of the same tool (e.g., multiple project management platforms)
-
Work being done on unmonitored devices
-
Inconsistent login behaviors or MFA prompts failing
-
Gaps in audit logs or sudden increases in data usage
At Halcyon Cyberworks, we help SMBs surface and address Shadow IT through:
-
Asset & Attack Surface Management (ASM): Detect unknown tools and services in use
-
Cloud Security Posture Management (CSPM): Monitor unsanctioned cloud use
-
AI-driven Workflow Automation: Alert and respond to Shadow IT activities in real-time
-
One Year Free Hot Log Storage: Audit past activity and anomalies with no extra cost
Mitigating Shadow IT Without Slowing Down Your Business
We understand that small teams need agility. That’s why Halcyon Cyberworks’ all-in-one platform is designed to protect without getting in the way.
What You Can Do Today:
-
✅ Set Clear IT Policies
Define which tools are allowed and how to request new ones -
✅ Provide Secure, Approved Alternatives
Offer pre-vetted tools for cloud storage, collaboration, and communication -
✅ Train Your Team
Use our Phishing Awareness and Cybersecurity Training services to help employees understand the dangers -
✅ Implement Security Controls That Scale
Our platform includes SIEM, XDR-as-a-Service, SOAR, RMM, and UEBA to give you full visibility and real-time response across users, devices, and apps -
✅ Engage with a vCISO or GRC-as-a-Service
Let our experts help you build policy, compliance, and governance frameworks without hiring full-time staff
Why Choose Halcyon Cyberworks?
HalcyonCyber offers a comprehensive, all-in-one platform designed specifically for SMBs, with AI-driven detection, automated response, and fully managed services — all at a fraction of the cost of hiring a full in-house team.
💡 Our platform brings together:
-
XDRaaS, SIEM, SOAR, UEBA, and SOC-as-a-Service
-
Secure email, DNS filtering, MFA, SSO, and password vault
-
Automated Incident Response, GRC, SECOPS, and Vulnerability Management
-
Staffing & Contracting Services when you need extra support or expertise
-
Cyber Insurance Partnership for added peace of mind
Best of all, it’s priced for small businesses — with plans starting at just $35/user/month.
Take Action Today
Shadow IT is already operating in the background of your business. Now is the time to bring it into the light and take control — before it becomes a headline.
✅ Book your FREE 30-minute consultation now
🔐 Take our FREE Cyber Defense Matrix assessment
📊 Gauge your compliance with our FREE NIST CSF v2 assessment
Visit www.halcyoncyber.works or call us at (555) 123-4567 to start your security transformation.