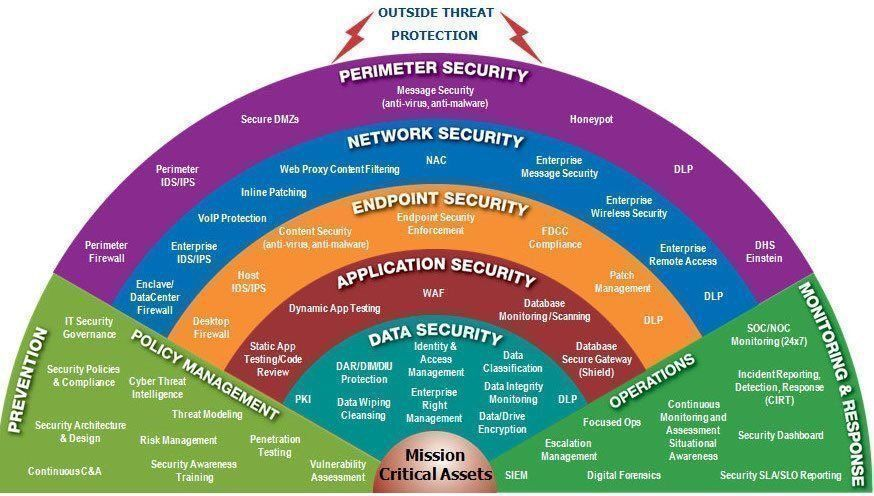
Modern Security Architecture: Moving Beyond Traditional Perimeter Security
Perimeter firewalls are yesterday’s defense. Learn how modern MSSPs leverage Zero Trust, Microsegmentation, and Threat-Informed Defense to deliver resilient, scalable protection.
In an era where threats don’t respect perimeters and ransomware kits are sold like SaaS, relying solely on traditional network defenses is like guarding your secrets with a picket fence. At ACME MSSP, we see this reality play out across small businesses and federal teams alike: legacy architectures just aren’t holding the line anymore.
It’s time to rethink what cybersecurity should look like in a post-perimeter world. Here’s how we do it.
1. Zero Trust Is Not a Buzzword—It’s a Baseline
Most attacks today don’t storm the gates—they log in through the front door. Password reuse, phishing, and token theft make internal traffic just as dangerous as external threats. Our Zero Trust model assumes no actor, system, or network is trustworthy by default.
Verification-first philosophy: Access is based on identity, device posture, location, and behavior.
Granular control: Role-based access, time-bound permissions, and enforced MFA.
Tooling: We deploy Identity Governance (IGA), Conditional Access, and Endpoint Detection (XDR) to enforce the Zero Trust lifecycle.
The result? Attackers may get in, but they don’t get far.
2. Microsegmentation Shrinks the Blast Radius
Even if attackers land inside your network, microsegmentation ensures their lateral movement is dead on arrival.
We isolate workloads and user access by sensitivity and risk profile.
East-west traffic is strictly inspected using policy-aware firewalls and behavior analysis.
Integration with SIEM and SOAR means abnormal movement triggers alerts and automated playbooks instantly.
For SMBs, we implement lightweight, agent-based segmentation that doesn’t require enterprise budgets. For government, we tailor segmentation to NIST 800-53 or CMMC requirements.
3. Threat-Informed Defense Using MITRE ATT&CK
Defending against threats you haven’t mapped is like playing chess blindfolded. That’s why we operationalize the MITRE ATT&CK framework:
Use-case development: Each detection in your SIEM is mapped to a specific ATT&CK technique.
Red/Blue collaboration: Purple team exercises validate whether your defenses are real or just theoretical.
Continuous testing: Automated breach & attack simulation tools feed into our SOC to close the loop on detection gaps.
We don’t just watch logs—we know what to look for and what to do when we find it.
4. SIEM + SOAR: Automation Without Overreach
Throwing every alert to a human analyst isn’t scalable. Our SOCaaS solution combines SIEM (for visibility) with SOAR (for orchestration) to turn chaos into clarity:
Tier-1 alerts are enriched and auto-triaged.
Known bad behaviors (e.g., credential stuffing, beaconing to known C2s) are blocked or isolated automatically.
Your human analysts focus only on decisions that need judgment, not noise.
And here’s the kicker: SMBs benefit from this enterprise-grade stack with none of the operational lift. We host, tune, and manage everything.
5. Compliance Without Complexity
Whether you’re aligning to NIST CSF, HIPAA, or DFARS, security needs to serve compliance—not the other way around. Our Governance, Risk, and Compliance (GRCaaS) offerings translate your technical controls into audit-ready evidence:
Pre-mapped frameworks in your portal (NIST, ISO, CMMC)
Continuous control monitoring via integrations with your stack
Automated policy creation, risk scoring, and task assignments
Security becomes proactive, not reactive—and you reduce audit fatigue while building resilience.
Final Thoughts
The perimeter is dead—but your security posture doesn’t have to be. By integrating Zero Trust, Microsegmentation, MITRE ATT&CK alignment, and SIEM+SOAR into a unified managed service, ACME delivers full-spectrum cybersecurity built for the complexity of today’s threats and the constraints of your budget.
Whether you’re an SMB securing a remote workforce or a federal contractor pursuing CMMC, we help you make every dollar count—while building a defense posture that’s light years ahead of static firewalls and ad-hoc alerts.