How Phishing Kits Are Evolving to Bypass MFA—and What SMBs Can Do
You implemented MFA and thought you were safe. Think again. Today’s phishing kits are smarter, faster, and built to sidestep even modern defenses. Here’s how your business can stay ahead—without stretching your security budget.
Introduction:
For years, Multi-Factor Authentication (MFA) has been touted as the silver bullet for account security. And rightly so—MFA blocks over 99% of credential-based attacks, according to Microsoft.
But cybercriminals adapt fast. And now, with a new breed of phishing kits capable of bypassing MFA, small and midsize businesses (SMBs) are being blindsided.
The reality is chilling: attackers no longer need to steal your passwords—they can steal your authenticated session instead.
At ACME MSSP, we specialize in helping SMBs and public sector entities stay one step ahead. Let’s walk you through how phishing kits are evolving, how they exploit weaknesses in user behavior and technology, and most importantly, how managed security services can stop them cold.
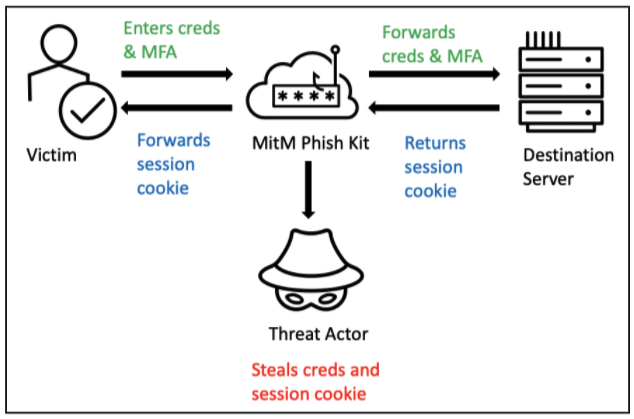
Part 1: The New Breed of Phishing Kits
Today’s phishing kits go far beyond the simplistic fake login pages of the past. The most advanced ones now support:
🔐 Reverse Proxy Functionality
Tools like Evilginx2, Modlishka, and Muraena sit between the victim and the real login portal.
The user logs in, completes MFA, and the attacker captures the session cookie/token.
Result: Full access without needing a password ever again.
📱 Real-Time Relay Attacks
Some kits are paired with Telegram bots that notify attackers instantly when a user submits credentials.
The attacker uses these credentials and MFA codes in real-time, often from the same region as the victim (to evade IP-based alerts).
🎭 Session Hijacking
Once the token is stolen, attackers use it to impersonate the user and navigate internal systems.
They can access cloud drives, CRMs, email systems, and even deploy ransomware.
🧠 AI-Enhanced Deception
Phishing sites now use real-time content mirroring, AI-written content, and custom subdomains that fool even vigilant users.
Some kits can even “brand hop” in real-time—if they detect a company email domain, they’ll serve a matching clone site.
Part 2: Why SMBs Are Especially at Risk
Most SMBs assume their implementation of MFA makes them immune to phishing. But attackers aren’t brute-forcing anymore—they’re tricking users into handing over authenticated sessions.
Here’s why SMBs are in the crosshairs:
Limited Security Awareness Training
Staff often aren’t trained on recognizing man-in-the-middle phishing kits or real-time social engineering attempts.
No Continuous Session Monitoring
Most businesses can’t track post-authentication anomalies like logins from different IPs or devices.
Lack of Threat Intelligence Integration
SMBs often don’t subscribe to commercial threat feeds that can detect these phishing kits when they’re first deployed.
Security Overload with Lean Teams
Even if alerts fire, they’re missed. There’s no 24/7 SOC, no automation, and no structured response plan.
Part 3: How ACME MSSP Protects You from MFA-Bypass Attacks
✅ Managed XDRaaS
Our Extended Detection and Response platform continuously monitors session behavior. We detect when an MFA-authenticated session suddenly shifts geographic locations or starts performing abnormal actions.
✅ SOAR-Powered Response Playbooks
If a session token is hijacked, our SOAR system:
Flags the anomaly
Invalidates sessions in real-time
Blocks the attacking IP/domain
Notifies users and resets credentials
All automated, with analyst review from our 24/7 SOCaaS team.
✅ Deceptive Defense (Honey Accounts & Decoys)
We deploy honey tokens and decoy accounts that act like bait. If a phishing kit tries to leverage these, it tips off our system before damage is done.
✅ Email & Domain Protection
We use DMARC, DKIM, and SPF enforcement, plus advanced email filtering to reduce phishing delivery by up to 98%. No phishing email, no problem.
✅ Cybersecurity Awareness Training
Phishing kits evolve fast—but so can your team. ACME provides ongoing micro-training, phishing simulations, and real-world attack walkthroughs tailored for SMBs.
✅ DNS Filtering & URL Rewriting
We block known malicious domains and analyze suspicious links. Real-time page scanning prevents users from reaching reverse proxy phishing kits.
Part 4: Real Results—Without the SOC Price Tag
Our services aren’t just effective—they’re efficient.
One client avoided a six-figure ransomware incident by catching a session token reuse attempt through XDR.
Another reduced phishing click rates by 72% after just two months of our simulation training and SOAR-led auto-responses.
An SMB in the healthcare sector now has 24/7 coverage without hiring a single full-time security analyst.
Conclusion: MFA Is Not a Finish Line—It’s a Starting Point
Multi-Factor Authentication is necessary—but no longer sufficient.
Phishing kits now bypass it like a speed bump. If your security stops at login, attackers won’t.
But with ACME MSSP, you don’t just get a stack of tools—you get integrated protection, automation, visibility, and a team that never sleeps.
Don’t just check a box—build true cyber resilience.
Let ACME show you how.